SANS 2015 Shmoo Challenge - Better late than never!
I'm patiently waiting for the SANS holiday challenge and thought I'd fill in the gap by revisiting my SANS 2015 Shmoo Challenge submission. Better late than never, right?
Back in 2015, I competed in SANS 2015 Shmoo Challenge and was one of the first 10 participants who successfully completed the challenge. By doing so, I won this fancy NetWars T-Shirt:
Normally these shirts are reserved for NetWars winners, so if you see someone wearing it, go talk to them - they did something cool!
Sans and Counterhack put on high production value infosec challenges each year, and winners often get prizes such as training, NetWars access, rare shirts, etc...and anyone can compete for free.
The best part about these challenges is that they maintain all of them so anyone can go back, as far as 2011, and still complete them which is just awesome!
Okay - Let's get into it
The end goal is to find the "phrase that pays" and send it in an email along with a brief write-up on how you solved each of the questions.
Answering each question will give you a secret which can then be used to unzip open_this_to_win.7z.
Here's how I did it
Question 1:
-----------
"Alice has sent Bob an encrypted file. Find it, decrypt it, and find the secret inside.
Look in the alice.pcap file to answer this question.
Hint: Alice is often quite chatty with Bob, and phrases she references could be useful to use as passwords (or passphrases). You won't need to use wordlists, mutation, or brute-force of any kind to decrypt the encrypted file."
Answer:
-----------
I used wireshark to open alice.pcap from the "question_assets" folder that you get after you unzip "SANS-2015-Shmoocon-Challenge.zip."
One of the first things I do with CTF pcaps is see what I can export from them. With this one, I exported files > SMB, and I got the "another_message.7z" file.
There was a conversation in the pcap file that basically said: "you'll have to check the website yourself", "my favorite...a game that blends hacking, first-person shooting, and role playing..." and in the end, when I went to the shmoocon.org, I found a title that referenced "Ghost in the Shellcode " and that was the PW for the 7z file.
The contents of which were:
Hiya, Bob!
As normal, I've encrypted this communication so that Eve can't listen in. Seriously, when will she give up?
Here's the secret: "Build It, Belay It, and Bring It On/"
Don't include the quotes.
P.S.
Are you free the weekend of January 16th? ShmooCon is coming up, and it'd be fun to see you there in person.
Question 2:
-----------
"Carol has used Firefox for Android to search for, browse, and save a particular image. A compressed copy of her /data/data/org.mozilla.firefox folder is in the question_assets folder, named "org.mozilla.firefox.tgz". Find the serial number of the lens used to take the download picture, which is the secret for this question.
Hint: You may have to use resources outside the org.mozilla.firefox folder to fully answer this question."
Answer:
-----------
After unzipping "org.mozilla.firefox.tgz", I used sqlite3 to read the downloads.sqlite file as seen below:
$ sqlite3 downloads.sqlite
Back in 2015, I competed in SANS 2015 Shmoo Challenge and was one of the first 10 participants who successfully completed the challenge. By doing so, I won this fancy NetWars T-Shirt:
Fancy NetWars T-Shirt
Normally these shirts are reserved for NetWars winners, so if you see someone wearing it, go talk to them - they did something cool!
Sans and Counterhack put on high production value infosec challenges each year, and winners often get prizes such as training, NetWars access, rare shirts, etc...and anyone can compete for free.
The best part about these challenges is that they maintain all of them so anyone can go back, as far as 2011, and still complete them which is just awesome!
Okay - Let's get into it
The end goal is to find the "phrase that pays" and send it in an email along with a brief write-up on how you solved each of the questions.
Answering each question will give you a secret which can then be used to unzip open_this_to_win.7z.
Here's how I did it
Question 1:
-----------
"Alice has sent Bob an encrypted file. Find it, decrypt it, and find the secret inside.
Look in the alice.pcap file to answer this question.
Hint: Alice is often quite chatty with Bob, and phrases she references could be useful to use as passwords (or passphrases). You won't need to use wordlists, mutation, or brute-force of any kind to decrypt the encrypted file."
Answer:
-----------
I used wireshark to open alice.pcap from the "question_assets" folder that you get after you unzip "SANS-2015-Shmoocon-Challenge.zip."
One of the first things I do with CTF pcaps is see what I can export from them. With this one, I exported files > SMB, and I got the "another_message.7z" file.
The contents of which were:
Hiya, Bob!
As normal, I've encrypted this communication so that Eve can't listen in. Seriously, when will she give up?
Here's the secret: "Build It, Belay It, and Bring It On/"
Don't include the quotes.
P.S.
Are you free the weekend of January 16th? ShmooCon is coming up, and it'd be fun to see you there in person.
Question 2:
-----------
"Carol has used Firefox for Android to search for, browse, and save a particular image. A compressed copy of her /data/data/org.mozilla.firefox folder is in the question_assets folder, named "org.mozilla.firefox.tgz". Find the serial number of the lens used to take the download picture, which is the secret for this question.
Hint: You may have to use resources outside the org.mozilla.firefox folder to fully answer this question."
Answer:
-----------
After unzipping "org.mozilla.firefox.tgz", I used sqlite3 to read the downloads.sqlite file as seen below:
$ sqlite3 downloads.sqlite
SQLite version 3.19.3 2017-06-27 16:48:08
Enter ".help" for usage hints.
sqlite> .tables
moz_downloads
sqlite> .dump moz_downloads
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE moz_downloads (id INTEGER PRIMARY KEY, name TEXT, source TEXT, target TEXT, tempPath TEXT, startTime INTEGER, endTime INTEGER, state INTEGER, referrer TEXT, entityID TEXT, currBytes INTEGER NOT NULL DEFAULT 0, maxBytes INTEGER NOT NULL DEFAULT -1, mimeType TEXT, preferredApplication TEXT, preferredAction INTEGER NOT NULL DEFAULT 0, autoResume INTEGER NOT NULL DEFAULT 0, guid TEXT);
INSERT INTO moz_downloads VALUES(1,'173974131.jpg','http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000','file:///storage/emulated/0/Download/173974131.jpg','',1392762252466744,1392762252537026,1,'http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000','',333764,333764,'','',0,0,'abwrZ5us7Wr2');
CREATE UNIQUE INDEX moz_downloads_guid_uniqueindex ON moz_downloads(guid);
COMMIT;
sqlite>
Enter ".help" for usage hints.
sqlite> .tables
moz_downloads
sqlite> .dump moz_downloads
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE moz_downloads (id INTEGER PRIMARY KEY, name TEXT, source TEXT, target TEXT, tempPath TEXT, startTime INTEGER, endTime INTEGER, state INTEGER, referrer TEXT, entityID TEXT, currBytes INTEGER NOT NULL DEFAULT 0, maxBytes INTEGER NOT NULL DEFAULT -1, mimeType TEXT, preferredApplication TEXT, preferredAction INTEGER NOT NULL DEFAULT 0, autoResume INTEGER NOT NULL DEFAULT 0, guid TEXT);
INSERT INTO moz_downloads VALUES(1,'173974131.jpg','http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000','file:///storage/emulated/0/Download/173974131.jpg','',1392762252466744,1392762252537026,1,'http://cbssanfran.files.wordpress.com/2013/07/173974131.jpg?w=1000','',333764,333764,'','',0,0,'abwrZ5us7Wr2');
CREATE UNIQUE INDEX moz_downloads_guid_uniqueindex ON moz_downloads(guid);
COMMIT;
sqlite>
Then I downloaded that image and ran exiftool, which is where I got the serial number.
# exiftool 173974131.jpg | grep -i serial
Serial Number : 088015001238
Lens Serial Number : 0000c15998
Question 3:
-----------
Once you've recovered the audio file, look at it carefully to find the secret."
Answer:
-----------
After unzipping the provided .gz file, I wanted to see what was deleted and so I did the following:
$ svn log -v file:///root/svn
------------------------------------------------------------------------
r4 | jeff | 2015-01-09 05:11:38 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /goals.txt
Added latest goals
------------------------------------------------------------------------
r3 | jeff | 2015-01-09 05:09:40 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
D /shmooster.mp3
Oh, drat, I wasn't supposed to include that. Deleting the audio file...
------------------------------------------------------------------------
r2 | jeff | 2015-01-09 05:07:32 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /shmooster.mp3
Funny audio I heard and VISUALIZED
------------------------------------------------------------------------
r1 | jeff | 2015-01-09 05:05:05 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /.bash_logout
A /.bashrc
A /.profile
Added contents of home directory
------------------------------------------------------------------------
Once I knew the MP3's filename, I then extracted the deleted mp3 by running the following commands:
svnadmin create --fs-type fsfs svn
svnadmin load svn/ < svn_2015.dump
svn checkout -r 2 file:///root/svn shmooster.mp3
I then used audacity to view the spectrogram of the file. At this point you may be asking - didn't WTG already do a post on audacity and spectrograms? To that I say: YES WE DID!
The waveform didn't look all that interesting:
Switching to the spectrogram view shows the following which certainly appears interesting:
Changing the setting to include frequencies from 0Hz to 20000Hz displays the whole QR Code:
Question 4:
-----------
"Eve suspects that one of Alice, Bob, or Carol might not be as innocent as they seem. She'll need your help to prove it, however. Examine the other three questions and their included files. Which user, based off their malicious behavior, might be a Cylon?
Once you know who it is, find that user's password, which is the secret for this question."
Answer:
-----------
For this one...
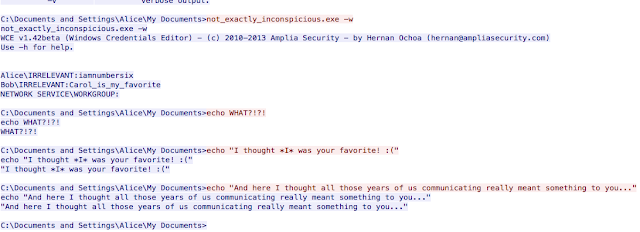
Well - it sorta assumes you know a little something about Battlestar Galactica. I've only ever seen the remake with Edward James Olmos but basically, tcp.stream == 1157 shows someone executing an .exe file, under the alice user's profile, that dumps cleartext passwords from the system. The passwords dumped imply that Alice is the 6th cylon based on a reference from the show.
So the four secrets from the questions are:
1) Build It, Belay It, and Bring It On/
2) 0000c15998
3) 3e9cd9ea80d80606
4) iamnumbersix
Now we have all of the secrets, we can unzip the "open_this_to_win.7z" file using the following password:
Build It, Belay It, and Bring It On/0000c159983e9cd9ea80d80606iamnumbersix
The file contents are as follows:
-strupo_
# exiftool 173974131.jpg | grep -i serial
Serial Number : 088015001238
Lens Serial Number : 0000c15998
Question 3:
-----------
"Dave messed up and deleted his only copy of an MP3 file. He'd really appreciate it if you could retrieve it for him - look inside svn_2015.dump.gz to get started.
Once you've recovered the audio file, look at it carefully to find the secret."
Answer:
-----------
After unzipping the provided .gz file, I wanted to see what was deleted and so I did the following:
$ svn log -v file:///root/svn
------------------------------------------------------------------------
r4 | jeff | 2015-01-09 05:11:38 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /goals.txt
Added latest goals
------------------------------------------------------------------------
r3 | jeff | 2015-01-09 05:09:40 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
D /shmooster.mp3
Oh, drat, I wasn't supposed to include that. Deleting the audio file...
------------------------------------------------------------------------
r2 | jeff | 2015-01-09 05:07:32 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /shmooster.mp3
Funny audio I heard and VISUALIZED
------------------------------------------------------------------------
r1 | jeff | 2015-01-09 05:05:05 -0500 (Fri, 09 Jan 2015) | 1 line
Changed paths:
A /.bash_logout
A /.bashrc
A /.profile
Added contents of home directory
------------------------------------------------------------------------
Once I knew the MP3's filename, I then extracted the deleted mp3 by running the following commands:
svnadmin create --fs-type fsfs svn
svnadmin load svn/ < svn_2015.dump
svn checkout -r 2 file:///root/svn shmooster.mp3
I then used audacity to view the spectrogram of the file. At this point you may be asking - didn't WTG already do a post on audacity and spectrograms? To that I say: YES WE DID!
The waveform didn't look all that interesting:
Boring.
To be fair though they rarely ever do.Switching to the spectrogram view shows the following which certainly appears interesting:
Looks like part of a QR Code.
Booya! Full QR Code.
At this point, back in 2015 - I'm sure that I installed some sort of QR reader and got the value that way. Today I just used google assistant, pressed the camera icon, and aimed it over the QR code and got the value:
Flag: 3e9cd9ea80d80606
-----------
"Eve suspects that one of Alice, Bob, or Carol might not be as innocent as they seem. She'll need your help to prove it, however. Examine the other three questions and their included files. Which user, based off their malicious behavior, might be a Cylon?
Once you know who it is, find that user's password, which is the secret for this question."
Answer:
-----------
For this one...
Well - it sorta assumes you know a little something about Battlestar Galactica. I've only ever seen the remake with Edward James Olmos but basically, tcp.stream == 1157 shows someone executing an .exe file, under the alice user's profile, that dumps cleartext passwords from the system. The passwords dumped imply that Alice is the 6th cylon based on a reference from the show.

Snippet from tcp.stream == 1157
So the four secrets from the questions are:
1) Build It, Belay It, and Bring It On/
2) 0000c15998
3) 3e9cd9ea80d80606
4) iamnumbersix
Build It, Belay It, and Bring It On/0000c159983e9cd9ea80d80606iamnumbersix
The file contents are as follows:
Congratulations! You've completed the challenge.
Alice, Bob, Carol, Dave, and Eve are very happy with your work.
...Well, maybe not Alice, but apparently she was a Cylon from the start.
Anyway, here's the last part of the challenge. Send an email with a brief write-up of how you solved each question to shmoochallenge2015@sans.org by February 28, 2015.
Use the following subject for the email: "The narwhal bacons at midnight."
To keep this challenge fun for others, please don't share this information with others before the Februrary 28, 2015 deadline :)
Thanks for playing!
lol - and here I am more than few years late, basically having to redo half of them...anyway - it was fun and I look forward to this year's holiday challenge.
-strupo_









